5.2 Service-Oriented Approach for Accountability in the Cloud
In section 2.3 it was established that cloud service provision chains are composed from heterogeneous elements which reside in separate control, trust and ownership domains. This creates challenges to establishing accountability across the chain, as strong accountability cannot be achieved without cross-domain access to certain controls and views of information, typically only available to the administrative entities inside each domain. To overcome this problem we have identified in section 2.4 a set of accountability artifacts that can be exchanged across domain boundaries to support accountability in a controlled manner without interfering with the structural properties of the boundaries themselves.
This approach achieves two critical goals:
- It promotes a model for accountability across cloud provisioning chains which is pragmatic, technology-agnostic and does not make unrealistic assumptions about the cloud environment. By developing a framework for evaluating accountability based only on the exchange of information in the form of accountability artifacts instead of requiring changes in the way clouds are architected, the desirable properties of cloud computing that emerge from the ability to flexibly compose services and abstract lower-level complexity are fully preserved. Overall accountability is achieved by establishing accountability over each direct service relationship formed.
- It does not dictate a one-size-fits-all approach. Every cloud actor can individually apply the accountability governance process in the way that makes sense to their business domain, organisational setup, capabilities and resources, as long as they can provide (and operate on) the required accountability artifacts in an interoperable way.
Accountability attributes can be generated via multiple combinations of potentially already-in-place and purpose-built systems and workflows of operations (e.g. existing logging systems re-configured to provide accountability-supporting machine-generated logs). In the A4Cloud Accountability RA we propose a technology-agnostic service-oriented approach to carry out the accountability functions and generate (or compile) and exchange the accountability artifacts. As illustrated in Figure 22, sets of services collectively designated as accountability support services, are operated internally by the various actors involved in a cloud service provisioning chain to support each actors primary operations by generating (or compiling) at the various phases of the lifetime of a service the necessary accountability artifacts that can be allowed to traverse control domain boundaries.
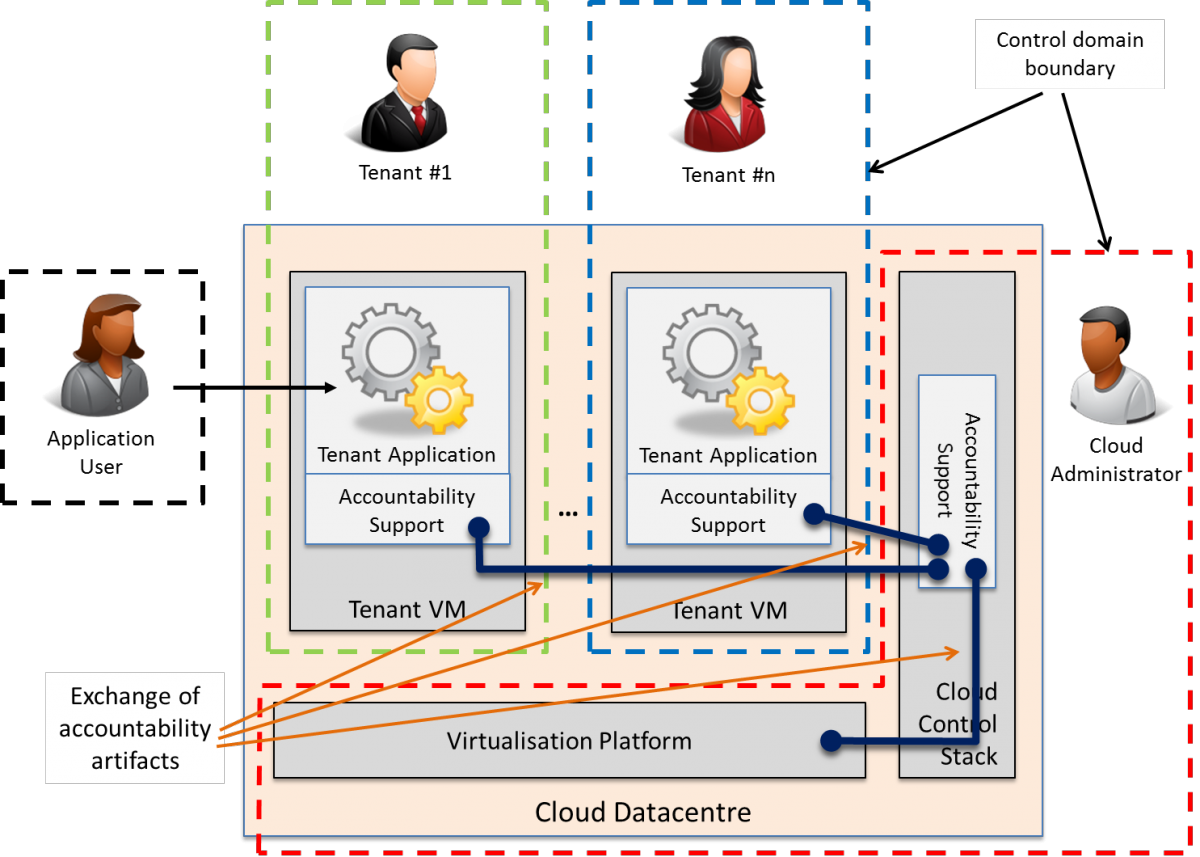
Figure 22: Supporting accountability via a service-oriented approach.
The A4Cloud RA does not dictate specific implementation requirements for the accountability support service model. Instead, we have identified a set of capabilities which participants must implement and integrate with their systems in a context-specific manner to develop the accountability support service suite that is suitable for their environment.

Figure 23: Accountability support services.
As illustrated in Figure 23, the RA Accountability Support Services are shown and then defined in Table 24:
|
Accountability Support Service |
Brief description |
|
Policy definition and validation |
Systems that enable and facilitate the definition and configuration of policies and validate that policy terms have been extracted properly from higher-level, human-readable documents such as SLAs, PLAs and contracts. |
|
Policy management & enforcement |
Enforcement covers systems that ensure operations (such as handling of data) are performed exclusively according to defined policies. Management covers systems that support the lifecycle of policies themselves, such as versioning, editing, testing, updating and deleting. |
|
Monitoring & environment state collection |
Systems that monitor, collect and store information on the state and operation of the various systems and components that comprise a particular cloud service . |
|
Collection & management of evidence |
Systems that collect and compile evidence records about the state and operation of designated elements of a cloud service, and manage their full lifecycle according to specific integrity, confidentiality and access control requirements . |
|
Incident management |
A collection of systems tasked with supporting and coordinating the incident management process . The exact capabilities and level of integration of systems comprising this accountability support service will vary between organisations but at the very least they will include functions such as recording and tracking incident management cases, compiling and processing information obtained from various databases and data stores (including monitoring data and evidence records), updating status of various processes and managing the content of notifications. |
|
Notification |
Systems that enable the formation, population and transmission of notification reports to authorised parties . |
|
Remediation |
Systems that assist in compiling and communicating remediation options to affected parties . |
|
Validation |
Systems that validate the extent of the ability of the systems (and their configurations) in place to support accountability assertions . |
Table 24: Accountability support services.
The rest of this section will focus on analysing these classes of accountability support services in more detail.
Download the preliminary release of the Cloud Accountability Reference Architecture and the relevant A4Cloud Toolkit.






